Password Security Best Practices
8-27-2021AVIBE employs several password security best practices when developing new web applications. In this blog post, we’ll touch on several password security methods:
- Encryption – One and Two-way
- Password Length & Brute Force
- Password Strength
- Login Attempts
Password Encryption
Encryption is crucial when an application is storing passwords in a database. Encryption encodes password data so it remains hidden. In the terrible event that a database becomes compromised, encrypted passwords are inaccessible. Encryption protects not only password data but private information and sensitive data like personal identifiable information (PII) or payment method information.
There are two types of encryption methods:
- Two-way
- One-way
Two-way encryption is reversible, meaning that passwords can be encrypted and stored but still are able to be deciphered and viewed again. One-way encryption is the preferred method. It’s irreversible and cannot be decoded in any way. This is done through “hashing”. Hashing is when plain text is turned into a fixed length hash so it cannot be decoded without considerable effort. When hashing, you take the password “test”, for example. The first step is to generate a “salt” for the password using the Java Random Library. This salt adds an additional value to the end of the password that changes the hash value produced. This extra step guarantees a unique output in the event where the hash inputs would be the same.
Password Length & Brute Force
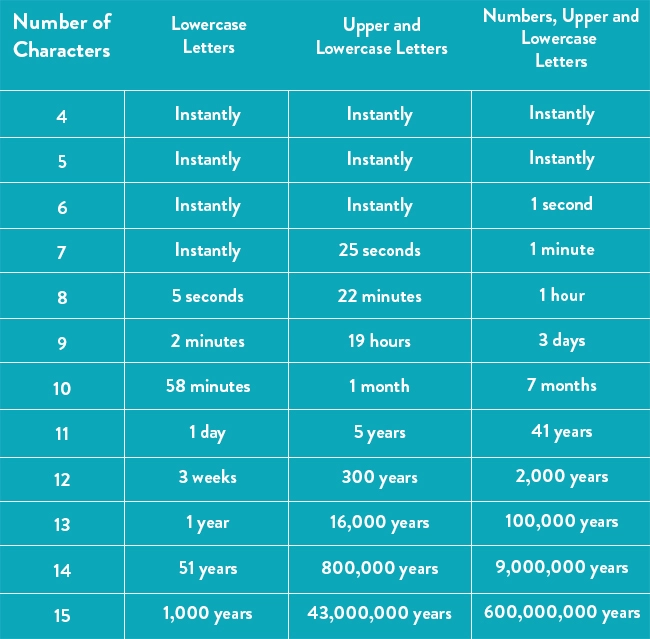
Most websites require that a password contains a minimum of eight characters. This is because of Moore’s Law. Moore’s Law is the perception that the number of transistors on a microchip doubles every two years. This means that over time, the number of transistors increases the power and capability to brute force password logging. Therefore, password length crack times become significantly smaller.
In 2015, a password length of eight characters would have taken around five hours to crack. Thanks to data from HowSecureIsMyPassword.net, using lowercase letters only and no special characters or numbers, it would take about five seconds to crack. Long story short, the longer the character length, the better. We recommend that your password length is 10 to 15 characters that includes capitalized letters, numbers, and special characters.
Password Strength
Password length alone isn’t going to stop someone from getting into a system with your password, you have to consider password strength. Password entropy is the measurement of how unpredictable a password is. This can be implemented into code alongside password libraries and dictionaries. Password libraries contain millions of passwords used that can be cross-referenced to notify users that the password they selected is in the library and cannot be used.
There are other libraries like ZXCVBN, which can help define “weak” passwords, recognize common word patterns, repeat characters, keyboard patterns and sequences (EX: ASDFGHJK), and Leet speak (EX: p@ssw0rd). Additionally, there is an API called, haveibeenpwned API which cross-references the password entered by the user against millions of passwords that have been exposed in previous data breaches. All of these libraries can help users select secure passwords.
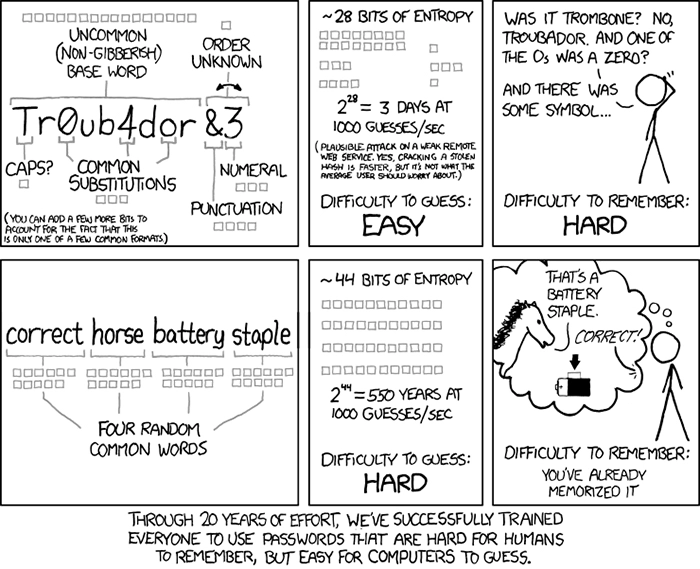
Image Credit: Xkcd.com
Prevent Scripting Spam Attempts
To prevent login and brute force attempts it is always a good idea to track login attempts and failed login attempts. By creating a login history table you can verify that the username inserted is actually a real username, track the date and time of login, and note if the login was successful. Logic can also be written to lock a user out of a system after too many failed login attempts within a certain time period. If the user account becomes locked after too many failed login attempts, users will be notified and prompted to reset their password.
Multi-Factor Authentication
Multi-Factor Authentication (MFA) is becoming more and more common to support login and password security. You see this on banking apps for example, which house sensitive personal information. It is an authentication method that requires the users to provide two or more verification factors to gain access to a web application. Here are three different authentication methods that are commonly used:
banking apps for example, which house sensitive personal information. It is an authentication method that requires the users to provide two or more verification factors to gain access to a web application. Here are three different authentication methods that are commonly used:
- Email – A link or code is sent to the email address on file, this code must be used along with the password to allow the user to login.
- Text – A link or code is texted to the phone number on file, this code must be used along with the password to allow the user to login.
- Authenticator – Apps that allow a user to add an account via QR code and generates a random numeric code only valid for X amount of time. This authentication method is not sent over the air like an email/text, it’s sent through a third-party application.
The Future of Passwords
It’s possible that in the future we move away from passwords all together and rely solely on authentications and bio identification methods (e.g., fingerprints, facial recognition, etc.) to gain access to applications. No longer relying on passwords would eliminate the need for users to remember and keep track of various passwords and keep user devices and account data secure from hackers. We are a ways away from not requiring passwords but don’t be surprised when that day comes.
Do you have trouble remembering all of your passwords? If you said no, you likely need to create more passwords. It’s not advised to use the same password across several applications. We recommend using a Password Manager like LastPass, to help keep track of all of your passwords and which application each password is associated with.

